Protect your corporate network from Shadow IT
Vaultry helps you identify unauthorized applications – like cracked software, and unapproved freemium programs – that pose serious risks to your company.
Protect your corporate network from Shadow IT
Vaultry helps you identify unauthorized applications – like overused license registrations, cracked software, and unapproved freemium programs – that pose serious risks to your company.

Avoid financial losses from non-compliance, ransomware, malware and data breaches
Vaultry Protection Layers
Stay compliant and safeguard your brand
Vaultry alerts you to risky applications to help prevent data leaks, reputational damage and non-compliance issues.
- Fingerprint analytics
- Scanning of files and folders
- Certificate tampering
- Keygen software monitoring
- and more ...
Easy deployment
Set up and deploy with ease
With just a few clicks, activate Vaultry within your network and monitor hundreds, or thousands, of devices at once.
Shadow IT, the trillion dollar threat to corporate networks
The use of unauthorized applications often exposes organizations to cyber threats.
For example, unlicensed software – where legitimate agreements have been exceeded – may appear trivial. However, this means the latest security patches and upgrades that fix vulnerabilities are not included, leading to serious risks.
If undetected, these programs can lead to serious financial losses as a result of data leaks, malware, ransomware or reputational damage.
In fact, data loss and downtime due to Shadow IT security breaches cost companies approximately $1.7 trillion each year.
49%
of cyberattacks were due to shadow IT
42%
of illegally downloaded software is infected with malware
40%
of individuals and teams use unauthorized software in their daily work
Defends organizations against unwanted activity
For IT managers and admins
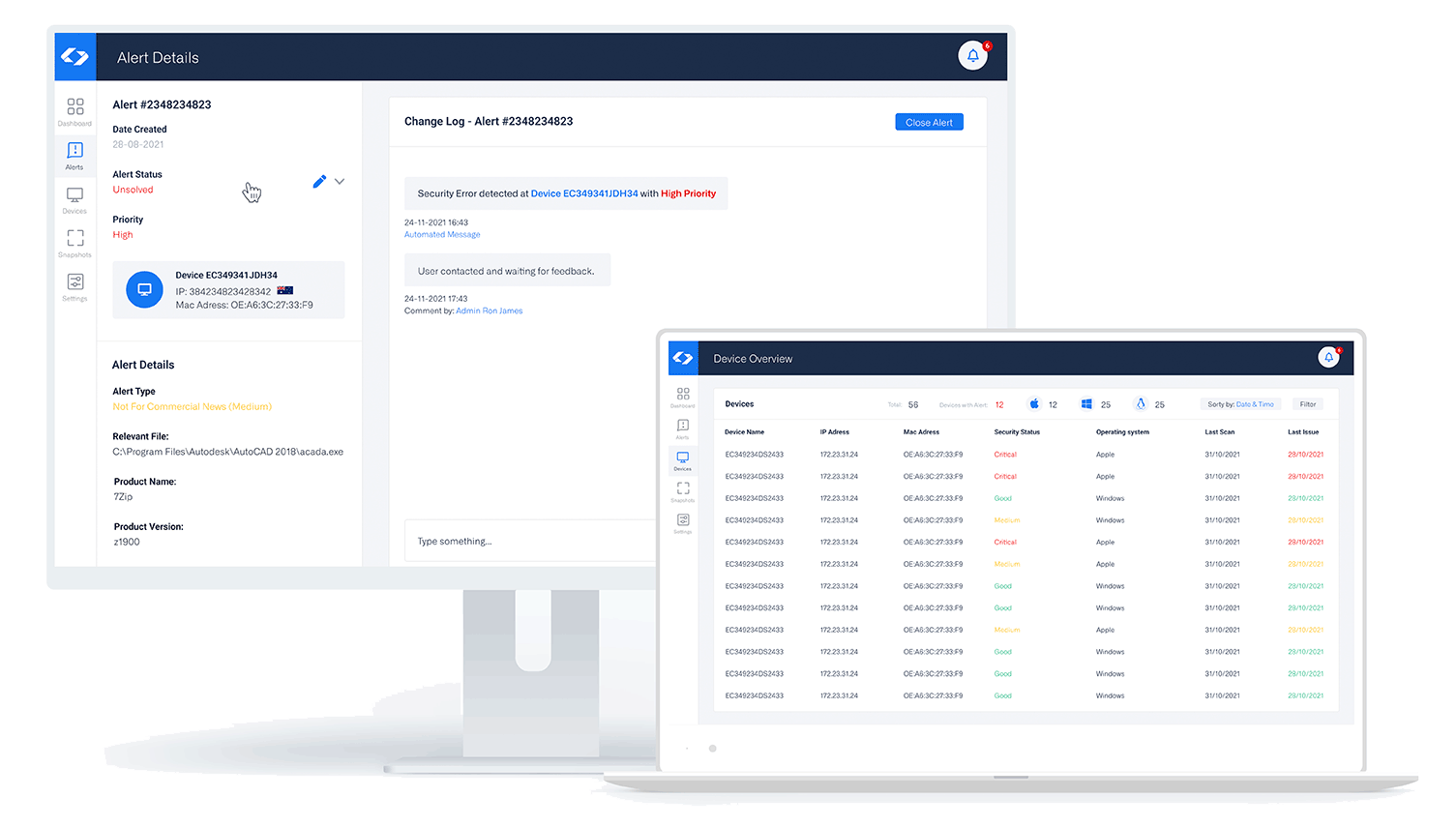
Vaultry protection layers:
- Fingerprint analytics
- Scanning of files and folders
- Certificate tampering
- Keygen software monitoring
- Unauthorized browser extensions identification
- Unsuitable tools radar (identify software like games or plugins)
Shadow IT protection in 4 steps
How Vaultry works
Protect Your Corporate Network From Shadow IT
Get started
Monitoring starts
Get notified
Take action
Why Vaultry?
Easy to use
The simple dashboard allows you to see potential threats at a glance
Fast set up
Within 30 minutes, you’ll have Vaultry installed and ready to protect your network
Affordable
At only $8 to $15 per device, Vaultry is incredibly cost effective